Active Directory
Active Directory
LDAP Signing and Channel Binding
There are three different policies that can be used to increase the security of LDAP clients connecting to a Windows Server domain controller. Two policies address signing requirements, one for the domain controllers and another for connecting clients. The third policy deals with channel binding requirements.
LDAP signing ensures the integrity of a client-server conversation by requiring that the parties involved digitally sign the data being sent. Signing does NOT encrypt traffic.
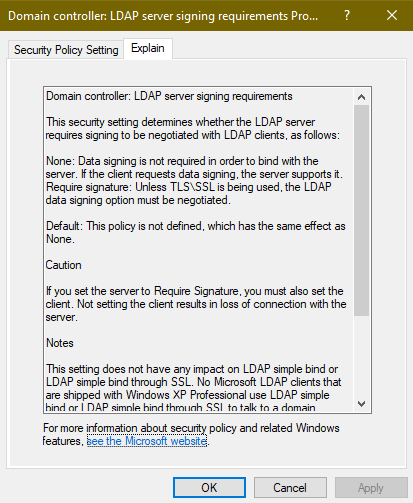
Server Signing Requirements
This policy only comes into play when LDAP connections are not using SSL/TLS encrypted communication. However, requiring LDAP signing is still worth doing because it adds additional protection in the event that LDAPS has not or can not be configured for a given client.
- GPO: Default Domain Controllers Policy
- Policy Location: Computer Configuration/Windows Settings/Security Policies/Local Policies/Security Options/Domain controller: LDAP server signing requirements
- Set policy to Require Signing
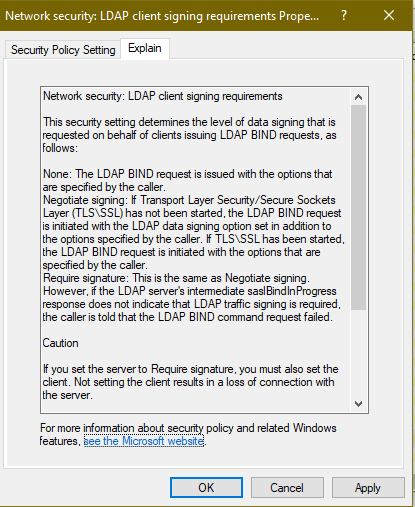
Client Signing requirements
This policy only comes into play when LDAP connections are not using SSL/TLS encrypted communication. However, requiring LDAP signing is still worth doing because it adds additional protection in the event that LDAPS has not or can not be configured for a given client.
- GPO: Default Domain Policy
- Policy Location: Computer Configuration/Windows Settings/Security Policies/Local Policies/Security Options/LDAP client signing requirements
- Set policy to Require Signing
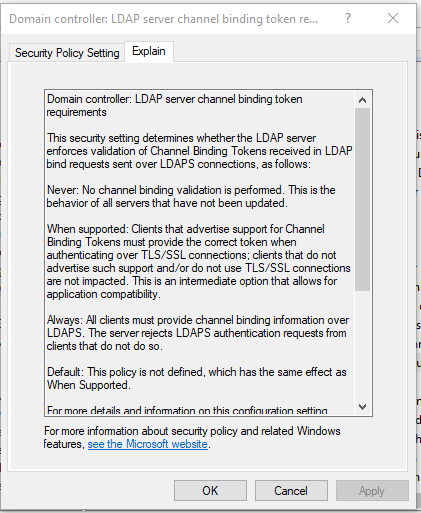
Channel Binding Token Requirements
Channel binding protects against the deliberate mismatch between authentication tokens and services being authenticated against. For example, an attacker could hijack a request from a compromised web server to do something malicious like create additional administrator accounts.
- GPO: Default Domain Controllers Policy
- Policy Location: Computer Configuration/Windows Settings/Security Policies/Local Policies/Security Options/Domain controller: LDAP server channel binding requirements
- Set policy to Always
LDAPS
LDAPS uses SSL/TLS to encrypt LDAP traffic. By default, Windows Server will listen for incoming LDAPS traffic on TCP port 636.
Windows Server will also accept unencrypted LDAP traffic on port 389, so it is still important to configure clients to use LDAPS whenever possible.

No comments to display
No comments to display