Hacking on ThinPro: Fixing EAP-TLS
I ran into a problem awhile ago which was causing ThinPro to strip an issuing CA out of a certificate chain. My investigation started when I noticed that wireless authentication for my test device was failing in certain areas. Naturally, I wanted to see what was going on with the wireless NIC, so I ran grep -i wlan0 /var/log/syslog to see if I could catch why it was so unhappy. I found the following information:
wlan0: CTRL-EVENT-EAP-TLS-CERT-ERROR reason=1 depth=0 subject='/C=US/ST=NY/L=HomeBase/O=NewbAdmin/OU=DummyOU/CN=DummyDev' err='unable to get local issuer certificate'
...
SSL: SSL3 alert: write (local SSL3 detected an error):fatal:unknown CA
EAP: Status notification: local TLS alert (param=unknown CA)
...
OpenSSL: openssl_handshake - SSL_connect error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failedSeeing the unknown CA alert, I thought maybe I had neglected to add a certificate, so I checked ThinPro's certificate control panel, but I didn't see anything missing. Next, I sent a SCEP enrollment task from HP Device Manager (HPDM) to see if ThinPro was breaking something during the enrollment process. Here's a screenshot of the chain before SCEP enrollment:
The purpose of a PKI certificate is to be public, but I used dummy certificates here anyway because why not.
-----BEGIN CERTIFICATE-----
MIIFVTCCAz2gAwIBAgIQMuoogkKW+69KyHGNg2JOcjANBgkqhkiG9w0BAQsFADA9
MRMwEQYKCZImiZPyLGQBGRYDT1JHMRQwEgYKCZImiZPyLGQBGRYEQ1JIQzEQMA4G
A1UEAxMHQ0gtUk9PVDAeFw0xNjEwMDcxODE5MjVaFw0zNjEwMDcxODI5MjNaMD0x
EzARBgoJkiaJk/IsZAEZFgNPUkcxFDASBgoJkiaJk/IsZAEZFgRDUkhDMRAwDgYD
VQQDEwdDSC1ST09UMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAvMJX
1O1aq68wauXbgr6lz5WsE85wZJGSZL3Uifx7QbWR8fsyY0avwUVXjXh98Cu8vfP1
Uqr4/ZsWsQQwNBnuaZQ5oc7+hpDMpJ0EOdhzG4sTj855H1xPgNvGEKdiMi2BE9OT
ZBTX1MDTM3tOuBX8lWPPQDIDJrelkjfioeur3908rdofjdslkg12hEE1eBnaNYRu
WoSxMqgEZd/f0/KDmSlWS6anx1rg/oX5SJY3Ct5IUYzCNkFdei7IBa9a9yUoomHb
aAwcrcGuZkmmZHryi0xizalzMPO9tLR7OQL7NfMm4NqEi567meERmIjY4cnVLBUk
fb/4Vg0ga9SzG1d3Z3it277/+HqoA64KLLevaEyfeaKgppv5DZ+lPMFxr06VZ5IO
meuMKgy5eQ5iuAizUAbnZ34DoZLzAKb3krPkLp+g1leEoWRHyA/fxz7aL0csl5xk
4bpQfy9UjEQkHQppdvBhKYU4fgnAhpZZ5Qi3c1EFM7WRCoDqTtZVP6dDMbDgOsPY
nzstE02KVst9ejN6CX2W+FAu31Nu8ZGxl+71LWpK5wjpIyQgZvVGiUxoryiJT4KV
T5bey33NrS/CYkKQCFaYihir9+kgzZ8YnJZs1/Rf58NTnOqMFG+1QwC6Teef0Daq
U07MlSmGZNygX1rkvXP0h5sabFrMsgw8LcKrHD3y3RFWSWWWWZ7CVzYe+XkhVdk0
ZnhEXcDO1IscWeKV+XQ1DZbhNt/DPmydEUgeIk0CAwEAAaNRME8wCwYDVR0PBAQD
6gzeMBAGCSsGAQQBgjcVAQQDAgEAMA0GCSqGSIb3DQEBCwUAA4ICAQAFk3tjjVdk
XdgyXR10Z1cyZrdGdUYOqimb/56FZDVFrGqoIIqmAzTrQJVHhGHtthVtQcfiGOcS
zoaxNPuxVflSNXIuG6yrxjPJdsvkxSSCAo9BwF+xhlt7f0S5rH/dVUg7zZCHcgDs
JPFIf8fbf/GrWAYXucE5VN2krYVUgX7kAObrFWSPZgTCcfMTkpCKrl91zVBSF6H/
Al9MtgZBfl+ZKaTNQzvheNrRO+o74YbENGdefNPDD1gr/fzykjwyuu6HfgYxZruK
X5SnBSo+eGSUogpVt+KFRvlSjRM1zH2nqwWXyrv/Gq7WUU6Lpl4njbCZTlvslfF6
uBflWB2nR/Fz9i6JLD9/AnwQhdJnVqBml6n9J1cE5IpE123454--====fdsatyFF
7E0FdPABMo8eIo9hPaplaZJy4dAr0gE0W1Rpya2T0gHCIAkkXH3eX3x9kB1XSYAT
aoY5BOtasgnbx5u6gdnc3ArBp2S92xCEjpuSj9QysysusmSi3OfOjVllBBU8BSbI
06EkoAIiJrIWl3lFqwpeWHf2/FCJwiKxXsevzYxjQBrbXpfzhE+fpSufzui7TwcG
AgGGMA8GA1UdEwEB/wQFMAMBAf8wHQYDVR0OBBYEFEpGDKYhVaVTF09zkyBGAeJi
DUzufkNofABNR7UA5LHEhQFy8smVlxRdVA==
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
06Knj/kX2gJk1LbNQzdf1mgCzLYc46jRdGQFiitIpmCJpTtDRcSPN1cmmQx+TJVC
MIIGVTCCBD2gAwIBAgITKwAAAAcraJRyrb6ESQAAAAAABzANBgkqhkiG9w0BAQsF
ADA9MRMwEQYKCZImiZPyLGQBGRYDT1JHMRQwEgYKCZImiZPyLGQBGRYEQ1JIQzEQ
MA4GA1UEAxMHQ0gtUk9PVDAeFw0yMTA4MDQxODM0MDZaFw0yNjA4MDQxODQ0MDZa
MD4xEzARBgoJkiaJk/IsZAEZFgNvcmcxFDASBgoJkiaJk/IsZAEZFgRjcmhjMREw
DwYDVQQDEwhDSYtP7cTe00j5L/W1ZN542dkQawK7e7jC1JU1NVRTCCAiIwDQYJKo
AKjYg58FVunE1ZMcydpfXcfS4WCIaQcxwWwc+SiNddVfqZbNa3z/UYKpiH8s8tY9
NWI2v7snp7iDUX5Lj2E1qAPlPNAelsq57gBHQXb+9/c8JbIzMvqAxlfxYvFypoor
Bl7H9Jdr/f2JYD1lLmNyrI0hAZVr2Bve/rZIhvcNAQEBBQADggIPADCCAgoCggIB
d3SnkM4beaaMOiiPQp9I004G2gylSVCcEQ6iggHhZSfhiqqow5mRmqlOBbO6xSJ+
8b6KeX562/siirtbekyvoPl50Y1zZsD31Rr3/2c5dmezqfS5PcOn0cLaK7v3/mkD
xyVx62tgWCu2rhVh3+fiDjYO9I19tqlD116WJ2dFYa1IL2eCa7HBt8venjVgMze+
F7E7Hj4TYR4Hr3SWLvxoHljDrIWozlo5rGCwxgJ67+IDhI0KVVEZ2kDCLUh92M+F
Ky/DwPv3jbs67v72P6Iql87ujLeL5txMnivtIhmixs1pNqeyz8puhpzPqjqd274O
ZS9v+njtS0Z8OnQLfEUcqlMG+Rq096m0Kwy6fNDc57jH6g/6QAWoPhnAr7dzo/Om
dVscF43qilLFFqIeE1LiztkmxKXj/1UAlI5DnGD2eZOixq33nAtBtusKkYiV++7v
9KLIStDvnmVjzukb2kEWAV+exKFGh9VDg/6cj1xMm9RZAgMBAAGjggFLMIIBRzAQ
BgkrBgEEAYI3FQEEAwIBATAjBgkrBgEEAYI3FQIEFgQUYiaiWjySpvycLw0vpqDP
mV5HaSowHQYDVR0OBBYEFBbpihkZfBQbYkry/iZwS3U4bXkcMBkGCSsGAQQBgjcU
AgQMHgoAUwB1AGIAQwBBMAsGA1UdDwQEAwIBhjAPBgNVHRMBAf8EBTADAQH/MB8G
A1UdIwQYMBaAFEpGDKYhVaVTF09zkyBGAeJi6gzeMEAGA1UdHwQ5MDcwNaAzoDGG
L2h0dHA6Ly9wa2lpc3N1ZS5jcmhjLm9yZy9jZXJ0ZW5yb2xsL0NILVJPT1QuY3Js
MFMGCCsGAQUFBr1NmusG51MbpwghObnLM5dPi5gwEBBEcwRTBDBggrBgEFBQcwAo
aGMub3JnL2NlcnRlbnJvbGwvUEtJUm9vdF9DSC1ST09ULmNydDANBgkqhkiG9w0B
AQsFAAOCAgEApi5Sc2xyROCKuXsrUeZigR6LUjnrgijN6B1cg2Js9QL5yYGuf788
pm+fDfl9+zzdqgAZg0wq3wwLGWK7RuiValOm1YKbvakpjD3vcvE1d+oUjh6awtGM
cMUsqrDQEejwTbEYVAxAPKODVaqC11l8nRiWQnjSTKK8mPkDkgLTuct7MTP+0gGL
yTipI6QP+LWIaEyuJkqK/sfxgv5WpnTbLOuvPmBzJeLY3aHR0cDovL3BraWlzc3V
cXCiI327GBS9nj0ei2vXXcISDkvYTO2okPyeajrYAfAd2e4LHFlyGS8ildSVgNya
JxFAG9xAdJXG4+8A0VYvV+2ABkxzS8c9cZeSL56DXu3zD/gAGw6qvU1kT/zGhUtw
BjaZPehg96YqZghtWQgekF5X06rVKLDfUr5zmaEA5f/ECfHZQ7Pv+T9GfBH5VQ+z
vULY4KPKVjci/q9d6Qt1jN1SCBf0D/jHQjsFYFRAAE22MKaRxfNNuNsmF6iStbSg
kTPaahdnOIjD3+ejSu2KSJPvOqFmJq+jMoYwQUhJI1/eDZRrKxtp4AUF23D3ptQg
DGaPhJQzcpRQERN9PGGiq6WI4sMuIXBBuz2IThU3wCqbciaphFqBwTc=
-----END CERTIFICATE-----As you can see, there are clearly two certificates in this chain, but after running the SCEP enrollment task, I found this:
-----BEGIN CERTIFICATE-----
MIIFVTCCAz2gAwIBAgIQMuoogkKW+69KyHGNg2JOcjANBgkqhkiG9w0BAQsFADA9
MRMwEQYKCZImiZPyLGQBGRYDT1JHMRQwEgYKCZImiZPyLGQBGRYEQ1JIQzEQMA4G
A1UEAxMHQ0gtUk9PVDAeFw0xNjEwMDcxODE5MjVaFw0zNjEwMDcxODI5MjNaMD0x
EzARBgoJkiaJk/IsZAEZFgNPUkcxFDASBgoJkiaJk/IsZAEZFgRDUkhDMRAwDgYD
VQQDEwdDSC1ST09UMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAvMJX
1O1aq68wauXbgr6lz5WsE85wZJGSZL3Uifx7QbWR8fsyY0avwUVXjXh98Cu8vfP1
Uqr4/ZsWsQQwNBnuaZQ5oc7+hpDMpJ0EOdhzG4sTj855H1xPgNvGEKdiMi2BE9OT
ZBTX1MDTM3tOuBX8lWPPQDIDJrelkjfioeur3908rdofjdslkg12hEE1eBnaNYRu
WoSxMqgEZd/f0/KDmSlWS6anx1rg/oX5SJY3Ct5IUYzCNkFdei7IBa9a9yUoomHb
aAwcrcGuZkmmZHryi0xizalzMPO9tLR7OQL7NfMm4NqEi567meERmIjY4cnVLBUk
fb/4Vg0ga9SzG1d3Z3it277/+HqoA64KLLevaEyfeaKgppv5DZ+lPMFxr06VZ5IO
meuMKgy5eQ5iuAizUAbnZ34DoZLzAKb3krPkLp+g1leEoWRHyA/fxz7aL0csl5xk
4bpQfy9UjEQkHQppdvBhKYU4fgnAhpZZ5Qi3c1EFM7WRCoDqTtZVP6dDMbDgOsPY
nzstE02KVst9ejN6CX2W+FAu31Nu8ZGxl+71LWpK5wjpIyQgZvVGiUxoryiJT4KV
T5bey33NrS/CYkKQCFaYihir9+kgzZ8YnJZs1/Rf58NTnOqMFG+1QwC6Teef0Daq
U07MlSmGZNygX1rkvXP0h5sabFrMsgw8LcKrHD3y3RFWSWWWWZ7CVzYe+XkhVdk0
ZnhEXcDO1IscWeKV+XQ1DZbhNt/DPmydEUgeIk0CAwEAAaNRME8wCwYDVR0PBAQD
6gzeMBAGCSsGAQQBgjcVAQQDAgEAMA0GCSqGSIb3DQEBCwUAA4ICAQAFk3tjjVdk
XdgyXR10Z1cyZrdGdUYOqimb/56FZDVFrGqoIIqmAzTrQJVHhGHtthVtQcfiGOcS
zoaxNPuxVflSNXIuG6yrxjPJdsvkxSSCAo9BwF+xhlt7f0S5rH/dVUg7zZCHcgDs
JPFIf8fbf/GrWAYXucE5VN2krYVUgX7kAObrFWSPZgTCcfMTkpCKrl91zVBSF6H/
Al9MtgZBfl+ZKaTNQzvheNrRO+o74YbENGdefNPDD1gr/fzykjwyuu6HfgYxZruK
X5SnBSo+eGSUogpVt+KFRvlSjRM1zH2nqwWXyrv/Gq7WUU6Lpl4njbCZTlvslfF6
uBflWB2nR/Fz9i6JLD9/AnwQhdJnVqBml6n9J1cE5IpE123454--====fdsatyFF
7E0FdPABMo8eIo9hPaplaZJy4dAr0gE0W1Rpya2T0gHCIAkkXH3eX3x9kB1XSYAT
aoY5BOtasgnbx5u6gdnc3ArBp2S92xCEjpuSj9QysysusmSi3OfOjVllBBU8BSbI
06EkoAIiJrIWl3lFqwpeWHf2/FCJwiKxXsevzYxjQBrbXpfzhE+fpSufzui7TwcG
AgGGMA8GA1UdEwEB/wQFMAMBAf8wHQYDVR0OBBYEFEpGDKYhVaVTF09zkyBGAeJi
DUzufkNofABNR7UA5LHEhQFy8smVlxRdVA==
-----END CERTIFICATE-----Yup, that would certainly do it. Something happened during the SCEP enrollment process that chopped out the second certificate. Also, RUDE!
Now that I could reproduce the problem on demand, I wanted to know when the OS started behaving this way, so I started rolling back updates. I started with SP8 and confirmed the issue was still present. The problem was also still present in SP7. It wasn't until I rolled back to SP2 that I was able to confirm that certificate chain processing was behaving correctly. So what changed?
Unfortunately, there wasn't anything helpful in the service pack release notes, so I had to manually update the OS and check the update log (hurray....) The first thing that caught my eye was that the hptc-cert-mgr package had been updated.
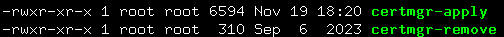
I found the /lib/hptc-cert-mgr/folder and took a look at the contents.
Hey, look at that! There's a script in there called certmgr-apply. That sure sounds promising. I compared the same script from SP2 and SP9. After confirming that the script had indeed been modified between versions, I reinstalled the copy from SP2 and re-ran the SCEP enrollment task. To my great relief, ThinPro was no longer breaking the chain during enrollment.
My experience with vendor support has been that more information = more better, so I decided to dig a little deeper before reporting the bug to HP. I compared the two copies of the certmgr-apply script and saw that there were only a few changes. I'll spare you the boring trip through most of the code, but my particular problem stems from this block here:
else
openssl x509 -in $CA_CERT_FILE -inform PEM -out $DEST_FILE.crt -outform PEM
if [ "$?" = "0" ]; then
echo "+${LOCAL_CERT_STORE}${DEST_FILE}.crt" >> ${CERTMGR_CHANGE_FILE}
rm $CA_CERT_FILE
fi
fiThis part of the script basically extracts the first certificate in the chain, outputs it to a new file, and then deletes the original chain. I'm not entirely sure what ultimate purpose this serves, but there is a very similar block of code with the same openssl command in both versions of the script, so I'll assume that it's at least trying to do something important.
The critical difference for me is actually closer to the top where some variables get declared. Here's the SP2 copy:
SUPPORT_SUFFIX=".crt .CRT"
UN_SUPPORT_SUFFIX=".pem .PEM"
TO_CONVERT_SUFFIX=".der .DER .p7b .P7B .p7c .P7C .cer .CER"And here's the SP7 copy:
SUPPORT_SUFFIX=""
UN_SUPPORT_SUFFIX=".pem .PEM"
TO_CONVERT_SUFFIX=".crt .CRT .der .DER .p7b .P7B .p7c .P7C .cer .CER"My walk through the script revealed that the removal of .crt from the SUPPORT_SUFFIX variable causes the certificate chain to be processed by the broken openssl command. The openssl command causes the issuing CA to be stripped out of the chain, and that results in ThinPro refusing to connect to the wireless network.
I hope someone out there on them internets finds this useful or at least mildly educational. Navigating a problem like this is rarely as quick or straightforward as it seems in the write-up, so remember to be patient and take it one step at a time.
Thanks for reading!

No comments to display
No comments to display