Learning PowerShell: Finding Users in Folder Permissions
One of the very first things you learn about when managing file and folder permissions (or any permissions, really) is that you should always assign permissions to groups, never individual users. That's all fine and wonderful if you're starting from scratch, but what if you've inherited an environment that had, we'll say, a less than optimal approach to permissions? Let's say you stumbled upon some network folders that do indeed have individual users listed in the ACLs. I bet you'd be curious to know how widespread the issue was.
Assuming you don't have some fancy GUI tool that'll handle this audit for you, you have a couple options.
Option 1 (slow and tedious and horrible): Open the folder properties, go to the security tab, manually check every object in the list, and repeat until you're sad and life becomes meaningless.
Option 2 (fast and awesome and FUN): Script it with PowerShell!
Given the title of this article, it's pretty obvious which option I'm going to go with. We're only doing an audit here, so it really won't require all that much digging and explaining.
Here's the script (see below for explanation).
# Get folder list
$Folders = Get-ChildItem -Directory
# Iterate through folders
foreach ($Folder in $Folders)
{
# Get just the name from the $Folder object then get permissions list
$FolderName = $Folder.FullName
$ACLObjects = (Get-Acl $FolderName).Access.IdentityReference.Value
Write-Host -ForegroundColor White -BackgroundColor DarkBlue $FolderName
# Iterate through objects returned in the permissions list
foreach ($Object in $ACLObjects)
{
$ObjectName = $Object.Split('\')[1]
try # Tries to get user information on the object. This'll error if the object is a group
{
Get-ADUser $ObjectName | Out-Null
Write-Host $ObjectName
}
catch # If error is encountered, the object is not a user and we don't care about it
{
Continue
}
}
}So, what did we do here? Here's a quick breakdown:
-
We start by listing folders with
Get-ChildItem -Directory -
Once we have our list of folders, we can iterate through them. Each
$Folderin$Foldersis an object with a bunch of properties, but we're just interested in the folder path, so we distill that out with$Folder.FullName. Once we have the name, we can pass that toGet-Aclto gather and store the permissions list. -
With the list in hand, we can iterate through each object and check if it is a user with
Get-ADUser(you'll need the Active Directory PowerShell module for this). Notice that we have to call the.splitmethod to strip the domain name off of the returned value. We don't care about the actual output here, so we'll just dump it by piping it toOut-Null. -
Get-ADUserwill error out if the object is something other than a user, in which case we just continue on to the next object. Note that you shouldn't use errors as a means of flow control in bigger projects, but this is meant to spit out a quick and dirty report, so I'm not going to spend too much time hack-proofing it. -
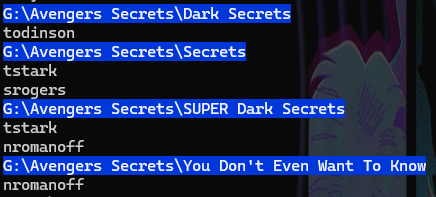
As the script runs, you'll see the folder path printed to the terminal window along with any individual users that can be removed from the ACL.
Executing the script will look something like this:
And that's really all there is to it. It's a little half-baked to just run the report without taking action and removing the offending users, but it's enough to at least determine how prevalent the problem is. This also won't really take into account objects about which the system doesn't know (unknown user accounts). I have an article here that can get you partially started on that, but know that you'll have to do some tweaking to get it to match this use case.
Thanks for reading!

No comments to display
No comments to display